Researchers at cybersecurity company AdaptiveMobile Security have released a report on a new vulnerability called Simjacker, which uses your smartphone’s SIM card to spy on you. Since Simjacker can use all brands and models of mobile phones, the vulnerability could affect more than 1 billion users.
The research firm believes the vulnerability was developed by a private company that works with governments to track the whereabouts of people around the world. An exploit can also help attackers obtain a unique IMEI number that belongs to each phone.
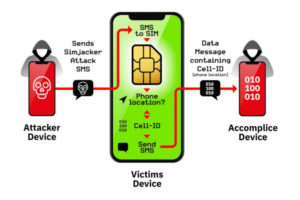
Some SIM cards supplied by mobile operators contain the so-called S @ T browser, which can be found in the SIM Application Toolkit. Simjacker sends a binary SMS message to the browser with instructions to get location data and an IMEI number and send information to a remote device using binary SMS as well. Since smartphones can use HTML browsers, the S @ T browser is out of date. Despite this fact, AdaptiveMobileSecurity found that operators in 30 countries, representing more than 1 billion mobile phone users, have active S @ T technology.
“Simjacker was subsequently used to carry out many other types of attacks on individuals and mobile operators, such as fraud, fraudulent calls, information leakage, denial of service and espionage. AdaptiveMobile Security Threat Intelligence analysts have seen how hackers modify their attacks by testing many of them. Theoretically, all brands and models of mobile phones are open to attack, since the vulnerability is associated with the technology built into the SIM card. The vulnerability of Simjacker can spread to more than 1 billion mobile phone users worldwide, which could potentially affect countries in North and South America, West Africa, Europe, the Middle East and any other region of the world that uses this SIM-card technology, ”writes AdaptiveMobileSecurity.
The report indicated that Simjacker tracks individuals daily, and some specific phone numbers are tracked hundreds of times over a seven-day period. Tracking a vulnerable phone requires a cheap GSM modem to send a message to a SIM card with S @ T browser technology. Using binary SMS, which differs from ordinary text messages, phones can be instructed to collect the requested information and transmit it to attackers. The study report notes that “during the attack, the user is completely unaware that he is a victim of the attack.”
The only consoling news is that the vulnerability relies on old technologies that should be minimized in theory. But until S @ T technology is completely removed from all SIM cards, Simjacker remains a threat. According to AdaptiveMobile Security CTO Catal McDade: “Now that this vulnerability has been discovered, we expect exploit authors and other attackers to try to develop these attacks in other areas.”
The GSM association says it was aware of Simjacker, and worked with researchers and the mobile industry to find out which SIM cards are vulnerable and how malicious messages can be blocked. It is suspicious that she was silent all this time.





